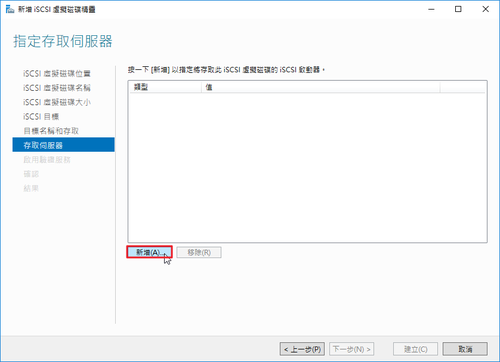
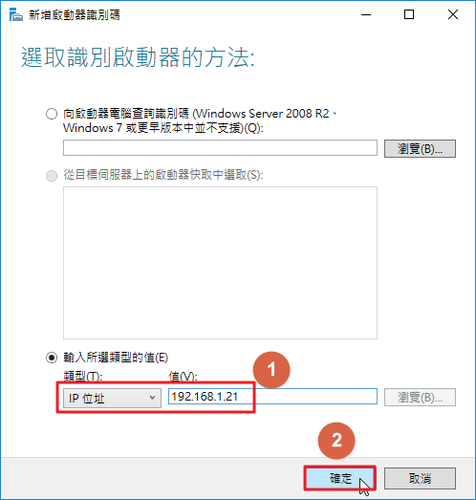
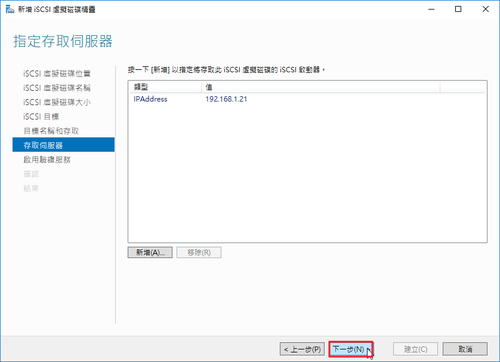
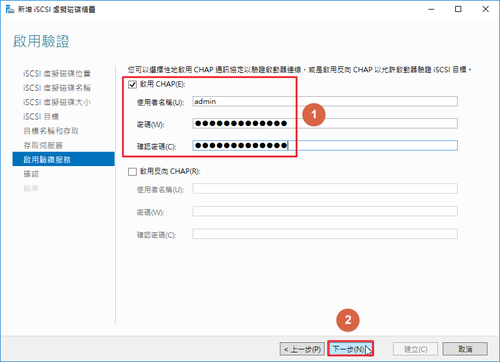
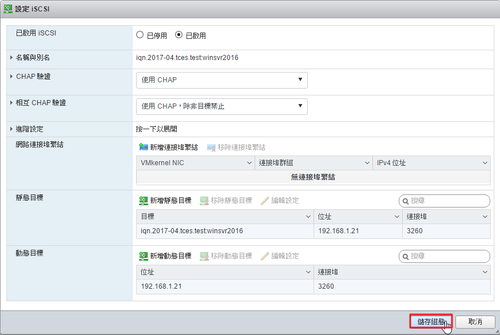
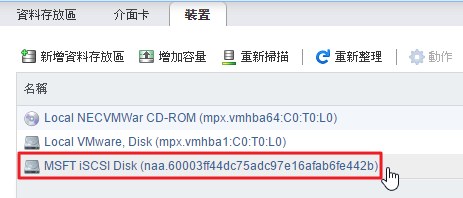
參考網頁:
鳥哥的 Linux 私房菜 — 網路磁碟裝置:iSCSI伺服器
iSCSI Target:192.168.1.18
iSCSI Initiator:192.168.1.20
1. 安裝 iSCSI Initiator
# yum install iscsi-initiator-utils
2. 修改 /etc/iscsi/initiatorname.iscsi 設定檔
# vim /etc/iscsi/initiatorname.iscsi
InitiatorName=iqn.2017-04.tces.test:centos6
3. 修改 /etc/iscsi/iscsid.conf 設定檔
# cp /etc/iscsi/iscsid.conf /etc/iscsi/iscsid.conf.$(date +%F)
# vim /etc/iscsi/iscsid.conf
把
#node.session.auth.authmethod = CHAP
#node.session.auth.username = username
#node.session.auth.password = password
修改成
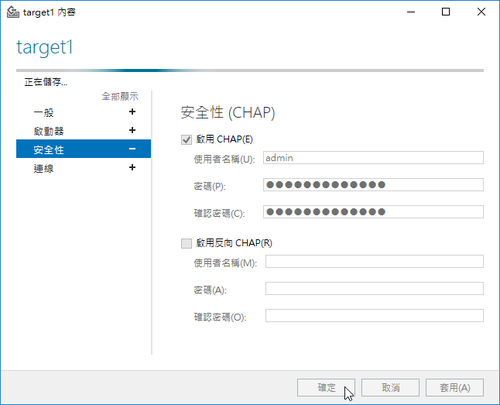
node.session.auth.authmethod = CHAP
node.session.auth.username = username
node.session.auth.password = password[@more@]
4. 啟用相關服務
# chkconfig –level 3 iscsi on
# /etc/init.d/iscsi start
# chkconfig –level 3 iscsid on
# /etc/init.d/iscsid start
5. 偵測 iSCSI Server 設備的相關資料
-m discovery :使用偵測的方式進行 iscsiadmin 指令功能;
-t sendtargets :透過 iscsi 的協定,偵測後面的設備所擁有的 target 資料
-p IP:port :就是那部 iscsi 設備的 IP 與埠口,不寫埠口預設是 3260
# /sbin/iscsiadm -m discovery -t sendtargets -p 192.168.1.18
192.168.1.18:3260,1 iqn.2017-04.tces.test:centos6-disk
6. 利用 iscsiadm 偵測到的 target 結果
# ll -R /var/lib/iscsi/nodes/
/var/lib/iscsi/nodes/:
total 4
drw——-. 3 root root 4096 Apr 9 12:49 iqn.2017-04.tces.test:centos6-disk
/var/lib/iscsi/nodes/iqn.2017-04.tces.test:centos6-disk:
total 4
drw——-. 2 root root 4096 Apr 9 12:49 192.168.1.18,3260,1
/var/lib/iscsi/nodes/iqn.2017-04.tces.test:centos6-disk/192.168.1.18,3260,1:
total 4
-rw——-. 1 root root 2117 Apr 9 12:49 default
7. 顯示目前系統上面所有的 target 資料
# /sbin/iscsiadm -m node
192.168.1.18:3260,1 iqn.2017-04.tces.test:centos6-disk
8. 登入使用
# /sbin/iscsiadm -m node -T iqn.2017-04.tces.test:centos6-disk -p 192.168.1.18 –login
Logging in to [iface: default, target: iqn.2017-04.tces.test:centos6-disk, portal: 192.168.1.18,3260] (multiple)
Login to [iface: default, target: iqn.2017-04.tces.test:centos6-disk, portal: 192.168.1.18,3260] successful.
9. 不使用時可以退出並刪除
# /sbin/iscsiadm -m node -T iqn.2017-04.tces.test:centos6-disk -p 192.168.1.18 –logout
Logging out of session [sid: 1, target: iqn.2017-04.tces.test:centos6-disk, portal: 192.168.1.18,3260]
Logout of [sid: 1, target: iqn.2017-04.tces.test:centos6-disk, portal: 192.168.1.18,3260] successful.
# /sbin/iscsiadm -m node
192.168.1.18:3260,1 iqn.2017-04.tces.test:esxi-disk
# /sbin/iscsiadm -m node -o delete
# /sbin/iscsiadm -m node
iscsiadm: No records found
10. 重新偵測一次
# /etc/init.d/iscsi restart
Stopping iscsi: [ OK ]
# /sbin/iscsiadm -m discovery -t sendtargets -p 192.168.1.18
192.168.1.18:3260,1 iqn.2017-04.tces.test:centos6-disk
# /sbin/iscsiadm -m node -T iqn.2017-04.tces.test:centos6-disk -p 192.168.1.18 –login
Logging in to [iface: default, target: iqn.2017-04.tces.test:centos6-disk, portal: 192.168.1.18,3260] (multiple)
Login to [iface: default, target: iqn.2017-04.tces.test:centos6-disk, portal: 192.168.1.18,3260] successful.
11. 新增的磁碟機
# fdisk -l /dev/sdb
WARNING: GPT (GUID Partition Table) detected on ‘/dev/sdb’! The util fdisk doesn’t support GPT. Use GNU Parted.
Disk /dev/sdb: 21.5 GB, 21474836480 bytes
255 heads, 63 sectors/track, 2610 cylinders
Units = cylinders of 16065 * 512 = 8225280 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 4194304 bytes
Disk identifier: 0x00000000
Device Boot Start End Blocks Id System
/dev/sdb1 1 2611 20971519+ ee GPT
12. 建立掛目錄及格式化硬碟
# mkdir /iscsidisk
# mkfs.ext4 /dev/sdb
mke2fs 1.41.12 (17-May-2010)
/dev/sdb is entire device, not just one partition!
Proceed anyway? (y,n) y
Filesystem label=
OS type: Linux
Block size=4096 (log=2)
Fragment size=4096 (log=2)
Stride=0 blocks, Stripe width=1024 blocks
1310720 inodes, 5242880 blocks
262144 blocks (5.00%) reserved for the super user
First data block=0
Maximum filesystem blocks=4294967296
160 block groups
32768 blocks per group, 32768 fragments per group
8192 inodes per group
Superblock backups stored on blocks:
32768, 98304, 163840, 229376, 294912, 819200, 884736, 1605632, 2654208,
4096000
Writing inode tables: done
Creating journal (32768 blocks): done
Writing superblocks and filesystem accounting information: done
This filesystem will be automatically checked every 27 mounts or
180 days, whichever comes first. Use tune2fs -c or -i to override.
13. 進行掛載
# mount /dev/sdb /iscsidisk
# df -h
Filesystem Size Used Avail Use% Mounted on
/dev/mapper/VolGroup-lv_root
18G 3.5G 13G 22% /
tmpfs 931M 0 931M 0% /dev/shm
/dev/sda1 477M 94M 358M 21% /boot
/dev/sdb 20G 44M 19G 1% /iscsidisk
14. 寫入 /etc/fstab,_netdev 代表這一個分割區是在網路上,要等開機網路啟動完成才會掛載
# vim /etc/fstab
/dev/sdb /iscsidisk ext4 defaults,_netdev 1 2