官方網站:
http://www.openvas.org/index.html
參考網站:
http://forums.atomicorp.com/viewtopic.php?f=31&t=8047
電腦筆記本: OpenVas8 on CentOS7
塵世浮沉近千秋: Cent OS 7 Install OpenVAS 8
OpenVAS6 – Itsmw
TWNIC 2015電子報
Install OpenVAS on CentOS 7 / RHEL 7
OpenVas – Itsmw
1) Disable SELINUX.
Edit /etc/selinux/config, save and reboot
# sed -i ‘s/SELINUX=enforcing/SELINUX=disabled/’ /etc/selinux/config
2) Add required packages
# yum install wget bzip2 texlive net-tools
3) Add Atomicorp repo
# wget -q -O – http://www.atomicorp.com/installers/atomic | sh
Do you agree to these terms? (yes/no) [Default: yes]
Configuring the [atomic] repo archive for this system
Installing the Atomic GPG keys: OK
Downloading atomic-release-1.0-21.el7.art.noarch.rpm: Preparing… ################################# [100%]
Updating / installing…
1:atomic-release-1.0-21.el7.art ################################# [100%]
OK
Enable repo by default? (yes/no) [Default: yes]:
The Atomic repo has now been installed and configured for your system
The following channels are available:
atomic – [ACTIVATED] – contains the stable tree of ART packages
atomic-testing – [DISABLED] – contains the testing tree of ART packages
atomic-bleeding – [DISABLED] – contains the development tree of ART packages
[@more@]4) Install OpenVAS
# yum update
# yum install openvas alien
5) edit /etc/redis.conf. Add/uncomment the following
unixsocket /tmp/redis.sock
unixsocketperm 700
# cp /etc/redis.conf /etc/redis.conf.$(date +%F)
# sed -i ‘s/^# unixsocket/unixsocket/’ /etc/redis.conf
6) Restart Redis
# systemctl enable redis && systemctl restart redis
# systemctl status redis
● redis.service – Redis persistent key-value database
Loaded: loaded (/usr/lib/systemd/system/redis.service; enabled; vendor preset: disabled)
Drop-In: /etc/systemd/system/redis.service.d
mqlimit.conf
Active: active (running) since 四 2017-02-09 15:16:46 CST; 40min ago
Main PID: 1030 (redis-server)
CGroup: /system.slice/redis.service
mq1030 /usr/bin/redis-server 127.0.0.1:6379
2月 09 15:16:46 localhost.localdomain systemd[1]: Started Redis persistent key-value database.
2月 09 15:16:46 localhost.localdomain systemd[1]: Starting Redis persistent key-value database…
7) openvas-setup
follow instructions. If rsync throws error, check that your network allows outgoing TCP 873 to internet
# /usr/bin/openvas-setup
Openvas Setup, Version: 1.0
Step 1: Update NVT, CERT, and SCAP data
Please note this step could take some time.
Once completed, this will be updated automatically every 24 hours
Select download method
* wget (NVT download only)
* curl (NVT download only)
* rsync
Note: If rsync requires a proxy, you should define that before this step.
Downloader [Default: rsync]
Updating NVTs….
[i] This script synchronizes an NVT collection with the ‘OpenVAS NVT Feed’.
[i] The ‘OpenVAS NVT Feed’ is provided by ‘The OpenVAS Project’.
[i] Online information about this feed: ‘http://www.openvas.org/openvas-nvt-feed.html’.
[i] NVT dir: /var/lib/openvas/plugins
[w] Could not determine feed version.
[i] rsync is not recommended for the initial sync. Falling back on http.
[i] Will use wget
[i] Using GNU wget: /usr/bin/wget
[i] Configured NVT http feed: http://www.openvas.org/openvas-nvt-feed-current.tar.bz2
[i] Downloading to: /tmp/openvas-nvt-sync.Q53foiaQhA/openvas-feed-2017-02-09-1275.tar.bz2
–2017-02-09 15:26:23– http://www.openvas.org/openvas-nvt-feed-current.tar.bz2
正在查找主機 www.openvas.org (www.openvas.org)… 5.9.98.186
正在連接 www.openvas.org (www.openvas.org)|5.9.98.186|:80… 連上了。
已送出 HTTP 要求,正在等候回應… 200 OK
長度: 28323931 (27M) [application/x-bzip2]
Saving to: ‘/tmp/openvas-nvt-sync.Q53foiaQhA/openvas-feed-2017-02-09-1275.tar.bz2’
Step 2: Configure GSAD
The Greenbone Security Assistant is a Web Based front end
for managing scans. By default it is configured to only allow
connections from localhost.
Allow connections from any IP? [Default: yes]
Redirecting to /bin/systemctl restart gsad.service
Step 3: Choose the GSAD admin users password.
The admin user is used to configure accounts,
Update NVT’s manually, and manage roles.
Enter administrator username [Default: admin] :
Enter Administrator Password:
Verify Administrator Password:
Redirecting to /bin/systemctl start redis.service
Setup complete, you can now access GSAD at:
https://<IP>:9392
Created symlink from /etc/systemd/system/multi-user.target.wants/openvas-scanner.service to /usr/lib/systemd/system/openvas-scanner.service.
Created symlink from /etc/systemd/system/multi-user.target.wants/openvas-manager.service to /usr/lib/systemd/system/openvas-manager.service.
Created symlink from /etc/systemd/system/multi-user.target.wants/gsad.service to /usr/lib/systemd/system/gsad.service.
8 ) To access OV-8 from network, either disable firewall or add exception for tcp 9392
# firewall-cmd –permanent –zone=public –add-port=9392/tcp
# firewall-cmd –reload
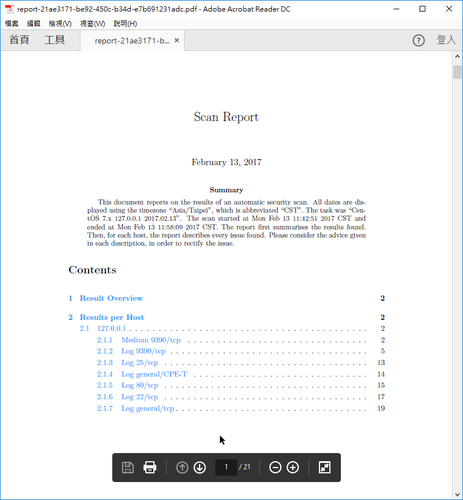
Go to https://<IP-ADDRESS>:9392 and login.
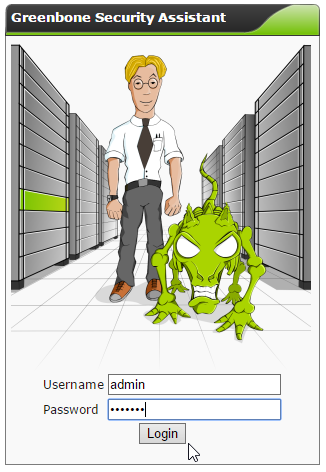
[Optional] : Greenbone Security Assistant (GSAD)
For those who wants to install proper SSL cert. Download certificate and key file to your CentOS box. I place them inside /etc/openvas/ssl.
Edit /etc/sysconfig/gsad and modify the OPTIONS tag e.g.
OPTIONS=”–ssl-certificate=/etc/openvas/ssl/openvas.crt –ssl-private-key=/etc/openvas/ssl/openvas.key”
Restart gsad
systemctl restart gsad
Those who wants stronger ciphers can will need to add gnutls-priorities, e.g.
OPTIONS=”–ssl-certificate=/etc/openvas/ssl/openvas.crt –ssl-private-key=/etc/openvas/ssl/openvas.key –gnutls-priorities=SECURE128:+SECURE192:-VERS-TLS-ALL:+VERS-TLS1.2″
(See explanation at http://gnutls.org/manual/html_node/Priority-Strings.html)
# openvas-check-setup
openvas-check-setup 2.3.7
Test completeness and readiness of OpenVAS-8
(add ‘–v6’ or ‘–v7’ or ‘–v9’
if you want to check for another OpenVAS version)
Please report us any non-detected problems and
help us to improve this check routine:
http://lists.wald.intevation.org/mailman/listinfo/openvas-discuss
Send us the log-file (/tmp/openvas-check-setup.log) to help analyze the problem.
Use the parameter –server to skip checks for client tools
like GSD and OpenVAS-CLI.
Step 1: Checking OpenVAS Scanner …
OK: OpenVAS Scanner is present in version 5.0.7.
OK: OpenVAS Scanner CA Certificate is present as /var/lib/openvas/CA/cacert.pem.
OK: redis-server is present in version v=3.0.7.
OK: scanner (kb_location setting) is configured properly using the redis-server socket: /tmp/redis.sock
OK: redis-server is running and listening on socket: /tmp/redis.sock.
OK: redis-server configuration is OK and redis-server is running.
OK: NVT collection in /var/lib/openvas/plugins contains 51765 NVTs.
WARNING: Signature checking of NVTs is not enabled in OpenVAS Scanner.
SUGGEST: Enable signature checking (see http://www.openvas.org/trusted-nvts.html).
OK: The NVT cache in /var/cache/openvas contains 51765 files for 51765 NVTs.
Step 2: Checking OpenVAS Manager …
OK: OpenVAS Manager is present in version 6.0.9.
OK: OpenVAS Manager client certificate is present as /var/lib/openvas/CA/clientcert.pem.
OK: OpenVAS Manager database found in /var/lib/openvas/mgr/tasks.db.
OK: Access rights for the OpenVAS Manager database are correct.
OK: sqlite3 found, extended checks of the OpenVAS Manager installation enabled.
OK: OpenVAS Manager database is at revision 146.
OK: OpenVAS Manager expects database at revision 146.
OK: Database schema is up to date.
OK: OpenVAS Manager database contains information about 51765 NVTs.
OK: At least one user exists.
OK: OpenVAS SCAP database found in /var/lib/openvas/scap-data/scap.db.
OK: OpenVAS CERT database found in /var/lib/openvas/cert-data/cert.db.
OK: xsltproc found.
Step 3: Checking user configuration …
WARNING: Your password policy is empty.
SUGGEST: Edit the /etc/openvas/pwpolicy.conf file to set a password policy.
Step 4: Checking Greenbone Security Assistant (GSA) …
OK: Greenbone Security Assistant is present in version 6.0.11.
Step 5: Checking OpenVAS CLI …
OK: OpenVAS CLI version 1.4.5.
Step 6: Checking Greenbone Security Desktop (GSD) …
SKIP: Skipping check for Greenbone Security Desktop.
Step 7: Checking if OpenVAS services are up and running …
OK: netstat found, extended checks of the OpenVAS services enabled.
OK: OpenVAS Scanner is running and listening on all interfaces.
OK: OpenVAS Scanner is listening on port 9391, which is the default port.
OK: OpenVAS Manager is running and listening on all interfaces.
OK: OpenVAS Manager is listening on port 9390, which is the default port.
OK: Greenbone Security Assistant is listening on port 9392, which is the default port.
Step 8: Checking nmap installation …
WARNING: Your version of nmap is not fully supported: 6.47
SUGGEST: You should install nmap 5.51 if you plan to use the nmap NSE NVTs.
Step 10: Checking presence of optional tools …
OK: pdflatex found.
OK: PDF generation successful. The PDF report format is likely to work.
OK: ssh-keygen found, LSC credential generation for GNU/Linux targets is likely to work.
OK: rpm found, LSC credential package generation for RPM based targets is likely to work.
WARNING: Could not find alien binary, LSC credential package generation for DEB based targets will not work.
SUGGEST: Install alien.
OK: nsis found, LSC credential package generation for Microsoft Windows targets is likely to work.
OK: SELinux is disabled.
It seems like your OpenVAS-8 installation is OK.
If you think it is not OK, please report your observation
and help us to improve this check routine:
http://lists.wald.intevation.org/mailman/listinfo/openvas-discuss
Please attach the log-file (/tmp/openvas-check-setup.log) to help us analyze the problem.