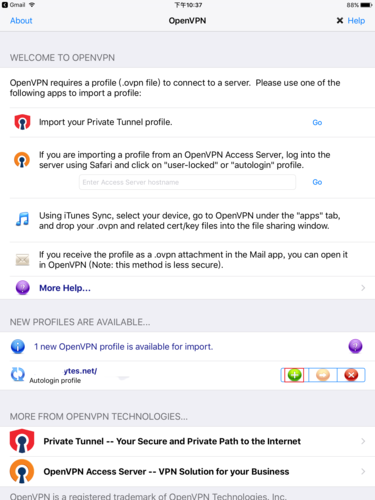
1. 在 Apple App Store 搜尋 OpenVPN Connect
OpenVPN Client – Android 手機篇
這裡以 Android 手機為例
1. 在 Google Play 商店搜尋 OpenVPN Connect,選擇 安裝
[@more@]2. 選擇 接受
6. 選擇 Import Profile from SD card
OpenVPN Client – macOS Sierra 系統篇
這裡使用的是 Tunnelblick 來做為 OpenVPN 的連線軟體。
Tunnelblick 下載網站:https://tunnelblick.net/downloads.html
這裡下載的是 Tunnelblick 3.6.9 Stable 版

[@more@]1. 在下載下來的檔案按滑鼠二下

OpenVPN Client – Windows 系統篇
1. 首先到 OpenVPN – Open Source VPN 網站下載 Client 所使用的程式:
或 https://openvpn.net/index.php/open-source/downloads.html
 [@more@]2. 依所使用的 Windows 版本下載
[@more@]2. 依所使用的 Windows 版本下載

5. 安裝過程
6. 將設定檔複製到 C:Program FilesOpenVPNconfig 目錄之下

8. 在右下角的 OpenVPN 圖示上按滑鼠右鍵,選擇 連接

9. 連線成功,會取得 IP,OpenVPN 圖示也會變成 綠色

OpenVPN Client 端設定
參考網頁:
CentOS 7 install OpenVPN @ 回憶……! :: 痞客邦 PIXNET ::
How To Set Up an OpenVPN Server on Ubuntu 16.04 | DigitalOcean
複製 OpenVPN Server 以下的這四個檔案至 OpenVPN Client Devices 上。
/etc/openvpn/easy-rsa/keys/ca.crt
/etc/openvpn/easy-rsa/keys/client.crt
/etc/openvpn/easy-rsa/keys/client.key
/etc/openvpn/easy-rsa/keys/ta.key
因為檔案比較多,為了使用者設定的方便,所以整合成一個 .ovpn 檔[@more@]建立存放檔案的目錄
# mkdir ~/openvpn_client_files
切換目錄
# cd /etc/openvpn/easy-rsa/keys/
複製 Client 端所需檔案
# cp ca.crt client.crt client.key ta.key ~/openvpn_client_files
建立 Client 端基本設定檔
# vim ~/openvpn_client_files/base.conf
client
dev tun
proto tcp
remote server_IP_address 1194
user nobody
group nogroup
persist-key
persist-tun
remote-cert-tls server
comp-lzo
verb 3
cipher AES-128-CBC
auth SHA256
key-direction 1
參考 How To Set Up an OpenVPN Server on Ubuntu 16.04 | DigitalOcean 建立 .ovpn 的 Script 檔
# vim ~/openvpn_client_files/make_config.sh
#!/bin/bash
# First argument: Client identifier
KEY_DIR=~/openvpn_client_files
OUTPUT_DIR=~/openvpn_client_files
BASE_CONFIG=~/openvpn_client_files/base.conf
cat ${BASE_CONFIG}
<(echo -e ‘<ca>’)
${KEY_DIR}/ca.crt
<(echo -e ‘</ca>n<cert>’)
${KEY_DIR}/${1}.crt
<(echo -e ‘</cert>n<key>’)
${KEY_DIR}/${1}.key
<(echo -e ‘</key>n<tls-auth>’)
${KEY_DIR}/ta.key
<(echo -e ‘</tls-auth>’)
> ${OUTPUT_DIR}/${1}.ovpn
更改檔案權限
# chmod 700 ~/openvpn_client_files/make_config.sh
切換目錄
# cd ~/openvpn_client_files
進行製作
# ./make_config.sh client
檢查是否有產生整合的設定檔
# ls -l ~/openvpn_client_files/*.ovpn
-rw-r–r– 1 root root 9860 12月 23 22:15 client.ovpn
active (exited) 和 active (running)
啟動 OpenVPN Server 後,檢查是否有正常運作
# systemctl start openvpn
# systemctl status openvpn
● openvpn.service – OpenVPN service
Loaded: loaded (/lib/systemd/system/openvpn.service; enabled; vendor preset:
Active: active (exited) since 五 2016-12-23 21:35:43 CST; 28s ago
使用 netstat 來檢查
# netstat -antp | grep :1194
tcp 0 0 0.0.0.0:1194 0.0.0.0:* LISTEN 3146/openvpn
似乎有正常運作[@more@]解決方式:
# systemctl start openvpn@server.service
# systemctl status openvpn@server.service
● openvpn@server.service – OpenVPN connection to server
Loaded: loaded (/lib/systemd/system/openvpn@.service; disabled; vendor preset
Active: active (running) since 五 2016-12-23 21:33:19 CST; 5s ago
關於這二者的說明,可以參考:
[Linux] systemctl 列出來的 loaded active exited 是什麼意思? @ 亂打一通的心情日記 :: 痞客邦 PIXNET ::
只不過我以前都是習慣使用前一種方式來執行
試用 Banana Pi R1 – Ubuntu minimal 16.04 上安裝 OpenVPN
參考網站:
How To Set Up an OpenVPN Server on Ubuntu 16.04 | DigitalOcean
1. 安裝 OpenVPN
# apt-get install openvpn easy-rsa
2. 建立 Certificate Authority
# mkdir -p /etc/openvpn/easy-rsa/keys
# cp -r /usr/share/easy-rsa /etc/openvpn
# cd /etc/openvpn/easy-rsa
請情況修改 /etc/openvpn/easy-rsa/vars 中的變數
# vim /etc/openvpn/easy-rsa/vars
export KEY_COUNTRY=”TW“
export KEY_PROVINCE=”Taiwan“
export KEY_CITY=”Yilan“
export KEY_ORG=”School“
export KEY_EMAIL=”me@myhost.mydomain”
export KEY_OU=”MyOrganizationalUnit”
# X509 Subject Field
export KEY_NAME=”EasyRSA”[@more@]
# source ./vars
NOTE: If you run ./clean-all, I will be doing a rm -rf on /etc/openvpn/easy-rsa/keys
# ./clean-all
# ./build-ca
3. 產生 Server 憑證、金鑰及加密檔案
# ./build-key-server server
Certificate is to be certified until Dec 21 10:24:53 2026 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
時間會稍微比較久一些
# ./build-dh
# openvpn –genkey –secret keys/ta.key
4. 產生 Client Certificate 和 Key Pair
# source ./vars
NOTE: If you run ./clean-all, I will be doing a rm -rf on /etc/openvpn/easy-rsa/keys
# ./build-key client
Please enter the following ‘extra’ attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Using configuration from /etc/openvpn/easy-rsa/openssl-1.0.0.cnf
Check that the request matches the signature
Signature ok
Certificate is to be certified until Dec 21 12:15:42 2026 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
如果要建立需要密碼
# source ./vars
NOTE: If you run ./clean-all, I will be doing a rm -rf on /etc/openvpn/easy-rsa/keys
# ./build-pass client
5. 複製憑證金鑰到 /etc/openvpn/keys 目錄
# cd /etc/openvpn/easy-rsa/keys
# mkdir /etc/openvpn/keys
# cp ca.crt ca.key server.crt server.key ta.key dh2048.pem /etc/openvpn/keys
6. 設定 OpenVPN
修改 /etc/openvpn/server.conf 設定檔
# gunzip -c /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz | tee /etc/openvpn/server.conf
# cp /etc/openvpn/server.conf /etc/openvpn/server.conf.$(date +%F)
修改設定
# sed -i ‘s/;tls-auth/tls-auth/’ /etc/openvpn/server.conf
# sed -i ‘/tls-auth/ akey-direction 0’ /etc/openvpn/server.conf
# sed -i ‘s/;cipher AES/cipher AES/’ /etc/openvpn/server.conf
# sed -i ‘/^cipher/ aauth SHA256’ /etc/openvpn/server.conf
OpenVPN 執行使用者及群組
# sed -i ‘s/^;user/user/’ /etc/openvpn/server.conf
# sed -i ‘s/^;group/group/’ /etc/openvpn/server.conf
VPN Client 的 Default Gatewa y以 VPN Gateway 為主
# sed -i ‘s/^;push “redirect/push “redirect/’ /etc/openvpn/server.conf
DNS 設定
# sed -i ‘s/^;push “dhcp-option DNS 208.67.222.222″/push “dhcp-option DNS 168.95.1.1″/’ /etc/openvpn/server.conf
# sed -i ‘s/^;push “dhcp-option DNS 208.67.220.220″/push “dhcp-option DNS 8.8.8.8″/’ /etc/openvpn/server.conf
將預設的 UDP 改為 TCP
# sed -i ‘s/^;proto tcp/proto tcp/’ /etc/openvpn/server.conf
# sed -i ‘s/^proto udp/;proto udp/’ /etc/openvpn/server.conf
更改 crt / key 的檔案位置
# sed -i ‘s|ca ca.crt|ca /etc/openvpn/keys/ca.crt|’ /etc/openvpn/server.conf
# sed -i ‘s|cert server.crt|cert /etc/openvpn/keys/server.crt|’ /etc/openvpn/server.conf
# sed -i ‘s|key server.key|key /etc/openvpn/keys/server.key|’ /etc/openvpn/server.conf
# sed -i ‘s|dh dh2048.pem|dh /etc/openvpn/keys/dh2048.pem|’ /etc/openvpn/server.conf
# sed -i ‘s|tls-auth ta.key 0|tls-auth /etc/openvpn/keys/ta.key 0|’ /etc/openvpn/server.conf
使用憑證認證時,允許所有的 Client 使用相同的 KEY 登入
# sed -i ‘s/^;duplicate-cn/duplicate-cn/’ /etc/openvpn/server.conf
允許 Client 間互接連接
# sed -i ‘s/^;client-to-client/client-to-client/’ /etc/openvpn/server.conf
更改 log 檔位置
# sed -i ‘s|status openvpn-status.log|status /var/log/openvpn/openvpn-status.log|’ /etc/openvpn/server.conf
# sed -i ‘s|;log openvpn.log|log /var/log/openvpn/openvpn.log|’ /etc/openvpn/server.conf
# sed -i ‘s|;log-append openvpn.log|log-append /var/log/openvpn/openvpn.log|’ /etc/openvpn/server.conf
此網段走 VPN Gateway
# sed -i ‘/^;push “route 192.168.10/ ipush “route 10.8.0.0 255.255.255.0″‘ /etc/openvpn/server.conf
For sed
# cat script-file
s/;tls-auth/tls-auth/
/tls-auth/ akey-direction 0
s/;cipher AES/cipher AES/
/^cipher/ aauth SHA256
s/^;user/user/
s/^;group/group/
s/^;push “redirect/push “redirect/
s/^;push “dhcp-option DNS 208.67.222.222″/push “dhcp-option DNS 168.95.1.1″/
s/^;push “dhcp-option DNS 208.67.220.220″/push “dhcp-option DNS 8.8.8.8″/
s/^;proto tcp/proto tcp/
s/^proto udp/;proto udp/
s|ca ca.crt|ca /etc/openvpn/keys/ca.crt|
s|cert server.crt|cert /etc/openvpn/keys/server.crt|
s|key server.key|key /etc/openvpn/keys/server.key|
s|dh dh2048.pem|dh /etc/openvpn/keys/dh2048.pem|
s|tls-auth ta.key 0|tls-auth /etc/openvpn/keys/ta.key 0|
s/^;duplicate-cn/duplicate-cn/
s/^;client-to-client/client-to-client/
s|status openvpn-status.log|status /var/log/openvpn/openvpn-status.log|
s|;log openvpn.log|log /var/log/openvpn/openvpn.log|
s|;log-append openvpn.log|log-append /var/log/openvpn/openvpn.log|
/^;push “route 192.168.10/ ipush “route 10.8.0.0 255.255.255.0”
# sed -i -f script-file /etc/openvpn/server.conf
建立存放 Log 的目錄
# mkdir /var/log/openvpn
7.設定網路 Forward
# sed -i ‘s/#net.ipv4.ip_forward=1/net.ipv4.ip_forward=1/’ /etc/sysctl.conf
# sysctl -p
8. 防火牆設定 iptables
# iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE
# iptables -A FORWARD -i tun0 -j ACCEPT
# iptables -A FORWARD -o tun0 -j ACCEPT
9. 設定開機時啟動 OpenVPN 服務
# systemctl enable openvpn@server.service
Created symlink from /etc/systemd/system/multi-user.target.wants/openvpn@server.service to /lib/systemd/system/openvpn@.service.
10. 啟動並檢查是否有正常啟動
# systemctl start openvpn@server.service
# systemctl status openvpn@server.service | head -3
● openvpn@server.service – OpenVPN connection to server
Loaded: loaded (/lib/systemd/system/openvpn@.service; enabled; vendor preset: enabled)
Active: active (running) since 五 2016-12-23 21:35:43 CST; 15h ago
# netstat -antpl | grep :1194
tcp 0 0 0.0.0.0:1194 0.0.0.0:* LISTEN 3146/openvpn
OpenVPN 無法正常啟動
1. 安裝及修改完 OpenVPN,要啟動時,卻出現錯誤
# systemctl start openvpn@server.service
Job for openvpn@server.service failed because the control process exited with error code. See “systemctl status openvpn@server.service” and “journalctl -xe” for details.
2. 檢查 OpenVPN 服務狀態
# systemctl status openvpn@server.service
● openvpn@server.service – OpenVPN Robust And Highly Flexible Tunneling Application On server
Loaded: loaded (/usr/lib/systemd/system/openvpn@.service; enabled; vendor preset: disabled)
Active: failed (Result: exit-code) since 二 2016-08-16 11:31:37 CST; 5min ago
Process: 1883 ExecStart=/usr/sbin/openvpn –daemon –writepid /var/run/openvpn/%i.pid –cd /etc/openvpn/ –config %i.conf (code=exited, status=1/FAILURE)
Main PID: 1845 (code=exited, status=0/SUCCESS)
8月 16 11:31:37 xxxxx.sytes.net systemd[1]: Starting OpenVPN Robust And Highly Flexible Tunneling Application On server…
8月 16 11:31:37 xxxxx.sytes.net openvpn[1883]: Options error: In [CMD-LINE]:1: Error opening configuration file: server.conf
8月 16 11:31:37 xxxxx.sytes.net openvpn[1883]: Use –help for more information.
8月 16 11:31:37 xxxxx.sytes.net systemd[1]: openvpn@server.service: control process exited, code=exited status=1
8月 16 11:31:37 xxxxx.sytes.net systemd[1]: Failed to start OpenVPN Robust And Highly Flexible Tunneling Application On server.
8月 16 11:31:37 xxxxx.sytes.net systemd[1]: Unit openvpn@server.service entered failed state.
8月 16 11:31:37 xxxxx.sytes.net systemd[1]: openvpn@server.service failed.
[@more@]3. 另外一種檢查方式
# journalctl -xe
— Unit openvpn@server.service has begun starting up.
8月 16 11:31:37 xxxxx.sytes.net openvpn[1883]: Options error: In [CMD-LINE]:1: Error opening configuration file: server.conf
8月 16 11:31:37 xxxxx.sytes.net openvpn[1883]: Use –help for more information.
8月 16 11:31:37 xxxxx.sytes.net systemd[1]: openvpn@server.service: control process exited, code=exited status=1
8月 16 11:31:37 xxxxx.sytes.net systemd[1]: Failed to start OpenVPN Robust And Highly Flexible Tunneling Application On server.
— Subject: Unit openvpn@server.service has failed
— Defined-By: systemd
— Support: http://lists.freedesktop.org/mailman/listinfo/systemd-devel
—
— Unit openvpn@server.service has failed.
—
— The result is failed.
8月 16 11:31:37 xxxxx.sytes.net systemd[1]: Unit openvpn@server.service entered failed state.
8月 16 11:31:37 xxxxx.sytes.net systemd[1]: openvpn@server.service failed.
8月 16 11:31:37 xxxxx.sytes.net polkitd[1816]: Unregistered Authentication Agent for unix-process:1878:1286078 (system bus name :1.37, object path /
看訊息似乎是無法開啟 /etc/openvpn/server.conf 設定檔
4. 檢查 /etc/openvpn/server.conf 檔案是否存在
# ls -l /etc/openvpn/server.conf
-rw-r–r–. 1 root root 10441 8月 16 11:30 /etc/openvpn/server.conf
5. 檔案正常存在,因為這一台 Server 有開啟 SELinux,所以檢查檔案的屬性
# ls -lZ /etc/openvpn/server.conf*
-rw-r–r–. root root unconfined_u:object_r:admin_home_t:s0 /etc/openvpn/server.conf
-rw-r–r–. root root unconfined_u:object_r:openvpn_etc_t:s0 /etc/openvpn/server.conf.20160816
6. 修改屬性
# chcon -t openvpn_etc_t /etc/openvpn/server.conf
7. 再檢查一次
# ls -lZ /etc/openvpn/server.conf*
-rw-r–r–. root root unconfined_u:object_r:openvpn_etc_t:s0 /etc/openvpn/server.conf
-rw-r–r–. root root unconfined_u:object_r:openvpn_etc_t:s0 /etc/openvpn/server.conf.20160816
8. 啟動 OpenVPN 服務
# systemctl start openvpn@server.service
# systemctl status openvpn@server.service
● openvpn@server.service – OpenVPN Robust And Highly Flexible Tunneling Application On server
Loaded: loaded (/usr/lib/systemd/system/openvpn@.service; enabled; vendor preset: disabled)
Active: active (running) since 二 2016-08-16 11:49:11 CST; 10s ago
Process: 1934 ExecStart=/usr/sbin/openvpn –daemon –writepid /var/run/openvpn/%i.pid –cd /etc/openvpn/ –config %i.conf (code=exited, status=0/SUCCESS)
Main PID: 1935 (openvpn)
CGroup: /system.slice/system-openvpn.slice/openvpn@server.service
mq1935 /usr/sbin/openvpn –daemon –writepid /var/run/openvpn/server.pid –cd /etc/openvpn/ –config server.conf
8月 16 11:49:11 xxxxx.sytes.net openvpn[1935]: GID set to nobody
8月 16 11:49:11 xxxxx.sytes.net openvpn[1935]: UID set to nobody
8月 16 11:49:11 xxxxx.sytes.net openvpn[1935]: Listening for incoming TCP connection on [undef]
8月 16 11:49:11 xxxxx.sytes.net openvpn[1935]: TCPv4_SERVER link local (bound): [undef]
8月 16 11:49:11 xxxxx.sytes.net openvpn[1935]: TCPv4_SERVER link remote: [undef]
8月 16 11:49:11 xxxxx.sytes.net openvpn[1935]: MULTI: multi_init called, r=256 v=256
8月 16 11:49:11 xxxxx.sytes.net openvpn[1935]: IFCONFIG POOL: base=10.8.0.4 size=62, ipv6=0
8月 16 11:49:11 xxxxx.sytes.net openvpn[1935]: IFCONFIG POOL LIST
8月 16 11:49:11 xxxxx.sytes.net openvpn[1935]: MULTI: TCP INIT maxclients=10 maxevents=14
8月 16 11:49:11 xxxxx.sytes.net openvpn[1935]: Initialization Sequence Completed
因為 /etc/openvpn/server.conf 是我直接複製別台修改好的設定檔,所以才會出現這樣的問題,也提醒自己使用 SELinux 應該注意的事項。
在 CentOS 7.x 上使用 OpenVPN
參考網站:
CentOS 7 install OpenVPN @ 回憶……! :: 痞客邦 PIXNET ::
CentOS 7 安裝 OpenVPN Server – Linux 技術手札
1. 安裝 epel 套件庫
# yum install epel-release
2. 安裝 OpenVPN 套件
# yum install openvpn
3. 安裝 Easy RSA 套件,之後要產生 Key 的
# yum install easy-rsa[@more@]4. 複製 server.conf 的範例檔至 openvpn 設定檔目錄
# cp /usr/share/doc/openvpn-*/sample/sample-config-files/server.conf /etc/openvpn
5. 備份原設定檔
# cp /etc/openvpn/server.conf /etc/openvpn/server.conf.$(date +%F)
6. 修改 /etc/openvpn/server.conf 設定檔
# egrep -v “^#|^$|^;” /etc/openvpn/server.conf
port 1194
proto tcp
dev tun
ca ca.crt
cert server.crt
key server.key # This file should be kept secret
dh dh2048.pem
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push “route 10.8.0.0 255.255.255.0”
push “redirect-gateway def1 bypass-dhcp”
push “dhcp-option DNS 168.95.1.1”
push “dhcp-option DNS 8.8.8.8”
client-to-client
duplicate-cn
keepalive 10 120
tls-auth ta.key 0 # This file is secret
comp-lzo
max-clients 10
user nobody
group nobody
persist-key
persist-tun
status openvpn-status.log
verb 3
7. 建立 Easy RSA 要產生 Key 的目錄
# mkdir -p /etc/openvpn/easy-rsa/keys
8. 複製 Easy RSA 範例檔至 Easy RSA 設定檔目錄
# cp -rf /usr/share/easy-rsa/2.0/* /etc/openvpn/easy-rsa
9. 請情況修改 /etc/openvpn/easy-rsa/vars 中的變數
export KEY_COUNTRY=”US”
export KEY_PROVINCE=”CA”
export KEY_CITY=”SanFrancisco”
export KEY_ORG=”Fort-Funston”
export KEY_EMAIL=”me@myhost.mydomain”
export KEY_OU=”MyOrganizationalUnit”
# X509 Subject Field
export KEY_NAME=”EasyRSA”
10. 以下為開始做建立憑證的動作:
# cp /etc/openvpn/easy-rsa/openssl-1.0.0.cnf /etc/openvpn/easy-rsa/openssl.cnf
# cd /etc/openvpn/easy-rsa
# source ./vars
NOTE: If you run ./clean-all, I will be doing a rm -rf on /etc/openvpn/easy-rsa/keys
# ./clean-all
# ./build-ca
# ./build-key-server server
# ./build-dh
# cd /etc/openvpn/easy-rsa/keys
# cp dh2048.pem ca.crt server.crt server.key /etc/openvpn
# cd /etc/openvpn/easy-rsa
# ./build-key client
11. 產生 ta.key
# cd /etc/openvpn/
# openvpn –genkey –secret ta.key
12. 安裝 iptables 的相關 packages 與設定 iptables
# yum install iptables-services -y
# systemctl mask firewalld
# systemctl enable iptables
Created symlink from /etc/systemd/system/basic.target.wants/iptables.service to /usr/lib/systemd/system/iptables.service.
# systemctl stop firewalld
# systemctl start iptables
# iptables –flush
13. iptables 防火牆上的設定
將 Source IP range 為 10.8.0.0/24 的 IP 做 NAT 後,並由 ppp0 出去
# iptables -A FORWARD -i tun0 -s 10.8.0.0/24 -j ACCEPT
# iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o ppp0 -j MASQUERADE
# iptables-save > /etc/sysconfig/iptables
# systemctl restart iptables
14. 修改 /etc/sysctl.conf 設定
# vim /etc/sysctl.conf
—————————————–
......
net.ipv4.ip_forward = 1
......
—————————————–
15. 啟動 OpenVPN 服務,並設定開機時啟動
# systemctl start openvpn@server.service
# systemctl enable openvpn@server.service
Created symlink from /etc/systemd/system/multi-user.target.wants/openvpn@server.service to /usr/lib/systemd/system/openvpn@.service.
16. 檢查 OpenVPN 服務狀態
# systemctl status openvpn@server.service
● openvpn@server.service – OpenVPN Robust And Highly Flexible Tunneling Application On server
Loaded: loaded (/usr/lib/systemd/system/openvpn@.service; enabled; vendor preset: disabled)
Active: active (running) since 日 2016-08-14 15:13:07 CST; 9s ago
Process: 2294 ExecStart=/usr/sbin/openvpn –daemon –writepid /var/run/openvpn/%i.pid –cd /etc/openvpn/ –config %i.conf (code=exited, status=0/SUCCESS)
Main PID: 2295 (openvpn)
CGroup: /system.slice/system-openvpn.slice/openvpn@server.service
mq2295 /usr/sbin/openvpn –daemon –writepid /var/run/openvpn/server.pid –cd /etc/openvpn/ –config server.conf
17. 檢查 OpenVPN 是否有正常啟動
# netstat -antulp | grep :1194
tcp 0 0 0.0.0.0:1194 0.0.0.0:* LISTEN 1039/openvpn
Cubie Truck 測試 – Arch Linux 安裝 OpenVPN Server
參考網頁:
OpenVPN – ArchWiki
Create a Public Key Infrastructure Using the easy-rsa Scripts – ArchWiki
頭城國小資訊組 | Banana Pi 測試 – Bananian 篇 安裝 OpenVPN Server
安裝 OpenVPN
# pacman -S openvpn easy-rsa
複製範例的設定檔到 /etc/openvpn 目錄
# cp -r /usr/share/easy-rsa /etc/openvpn
修改憑證預設資訊
# sed -i ‘s/KEY_COUNTRY=”US”/KEY_COUNTRY=”TW”/’ /etc/openvpn/easy-rsa/vars
# sed -i ‘s/KEY_PROVINCE=”CA”/KEY_PROVINCE=”Taiwan”/’ /etc/openvpn/easy-rsa/vars
# sed -i ‘s/KEY_CITY=”SanFrancisco”/KEY_CITY=”E-Land”/’ /etc/openvpn/easy-rsa/vars
# sed -i ‘s/KEY_ORG=”Fort-Funston”/KEY_ORG=”Home”/’ /etc/openvpn/easy-rsa/vars
[@more@]
切換目錄 /etc/openvpn/easy-rsa
# cd /etc/openvpn/easy-rsa
開始建立憑證
# source ./vars
NOTE: If you run ./clean-all, I will be doing a rm -rf on /etc/openvpn/easy-rsa/keys
清空舊有憑證
# ./clean-all
建立所需憑證
# ./build-ca
# ./build-key-server CubieTruck
# ./build-dh
# ./build-key Cubier
產生 ta.key
# openvpn –genkey –secret /etc/openvpn/easy-rsa/keys/ta.key
切換到 /etc/openvpn/easy-rsa/keys 目錄
# cd /etc/openvpn/easy-rsa/keys
複製 Server 端的檔案到 /etc/openvpn
# cp ta.key ca.crt ca.key dh2048.pem CubieTruck.crt CubieTruck.key /etc/openvpn
建立用來存放 Client 端所須檔案的目錄
# mkdir $HOME/openvpn-client-files
複製 Client 端所須檔案
# cp ca.crt Cubier.crt Cubier.key $HOME/openvpn-client-files
更改檔案名稱
# mv $HOME/openvpn-client-files/ca.crt $HOME/openvpn-client-files/capi.crt
更改檔案權限
# chmod +r $HOME/openvpn-client-files/Cubier.key
建立 /etc/openvpn/server.conf 設定檔
# vim /etc/openvpn/server.conf
port 1194
proto tcp
dev tun
;; Key File 設定
dh /etc/openvpn/dh2048.pem
ca /etc/openvpn/ca.crt
cert /etc/openvpn/CubieTruck.crt
key /etc/openvpn/CubieTruck.key
tls-auth /etc/openvpn/ta.key 0
;; vpn 使用網段
server 10.8.0.0 255.255.255.0
cipher AES-256-CBC
comp-lzo
persist-key
persist-tun
status openvpn-status.log
verb 3
tun-mtu 1500
tun-mtu-extra 32
mssfix 1450
;; 允許 client 間互相連接
;client-to-client
push “redirect-gateway def1”
;; DNS 設定
push “dhcp-option DNS 168.95.1.1”
push “dhcp-option DNS 140.111.66.1”
keepalive 5 30
;; 最大使用者量
max-clients 12
user nobody
group nobody
測試 /etc/openvpn/server.conf 設定檔語法是否正確
# openvpn /etc/openvpn/server.conf
防火牆上的設定,如果原本就有防火牆,就要將規則做整合
# vim /etc/firewall.vpn
#!/bin/bash
# Enable ip_forward
echo “1” > /proc/sys/net/ipv4/ip_forward
iptables -t filter -F
iptables -t nat -F
iptables -A FORWARD -m state –state RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWARD -s “10.8.0.0/24” -j ACCEPT
iptables -A FORWARD -j REJECT
iptables -t nat -A POSTROUTING -s “10.8.0.0/24” -j MASQUERADE
更改檔案權限
# chmod 700 /etc/firewall.vpn
設定開機時執行
在 /etc/rc.local 檔案最後面加入執行防火牆規則的設定
# sed -i ‘$a # OpenVPN 防火牆nsh /etc/firewall.vpn’ /etc/rc.local
執行 OpenVPN Server
# systemctl start openvpn@server.service
設定開機時執行 OpenVPN Server
# systemctl enable openvpn@server.service
檢查 OpenVPN Server 執行狀態
# systemctl status openvpn@server.service
檢查 OpenVPN Server 是否有正常執行
# netstat -antpul | grep openvpn
tcp 0 0 0.0.0.0:1194 0.0.0.0:* LISTEN 3682/openvpn
tun0 介面資訊
# ip addr show tun0
7: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UNKNOWN group default qlen 100
link/none
inet 10.8.0.1 peer 10.8.0.2/32 scope global tun0
解決出現 Failed to read PID from file /run/openvpn@server.pid: Invalid argument 的訊息
# chown nobody:nobody /var/run/openvpn@server.pid