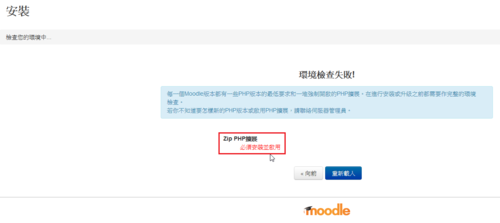
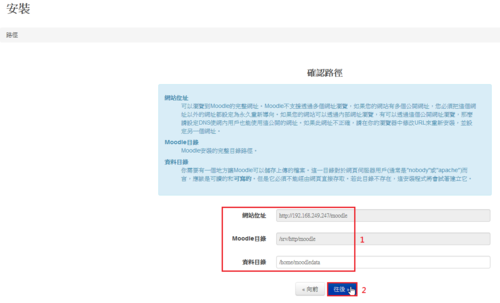
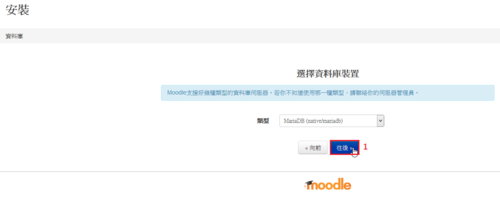
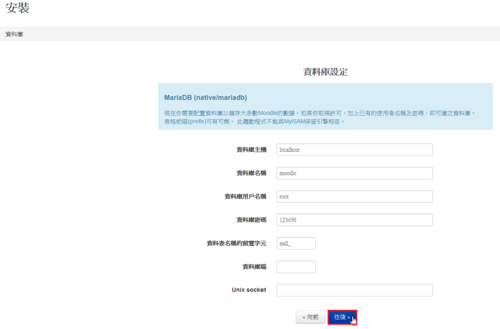
雖然 IPv6 目前在家裡使用的機率不是很高,但在學校裡使用是必要的。
預設使用的 Raspberry Pi ArchLinux 預設把 IPv6 的設定關掉。
# cat /boot/cmdline.txt
ipv6.disable=1 avoid_safe_mode=1 selinux=0 plymouth.enable=0 smsc95xx.turbo_mode=N dwc_otg.lpm_enable=0 console=ttyAMA0,115200 kgdboc=ttyAMA0,115200 console=tty1 root=/dev/mmcblk0p5 rootfstype=ext4 elevator=noop rootwait libahci.ignore_sss=1
開啟 IPv6 功能
修改前先備份原檔
# cp /boot/cmdline.txt /boot/cmdline.txt.$(date +%F)[@more@]
修改設定檔
# vim /boot/cmdline.txt
avoid_safe_mode=1 selinux=0 plymouth.enable=0 smsc95xx.turbo_mode=N dwc_otg.lpm_enable=0 console=ttyAMA0,115200 kgdboc=ttyAMA0,115200 console=tty1 root=/dev/mmcblk0p5 rootfstype=ext4 elevator=noop rootwait libahci.ignore_sss=1
重新啟動電腦
# systemctl reboot
檢查是否有取得 IPv6
# ifconfig eth0 | grep -m 1 inet6
inet6 2001:288:a229:2:ba27:ebff:fe31:70a5 prefixlen 64 scopeid 0x0<global>
檢查是否能以 IPv6 ping 到外部
# ping6 -c 4 2001:288:a229:1::250
PING 2001:288:a229:1::250(2001:288:a229:1::250) 56 data bytes
64 bytes from 2001:288:a229:1::250: icmp_seq=1 ttl=64 time=1.80 ms
64 bytes from 2001:288:a229:1::250: icmp_seq=2 ttl=64 time=0.502 ms
64 bytes from 2001:288:a229:1::250: icmp_seq=3 ttl=64 time=0.470 ms
64 bytes from 2001:288:a229:1::250: icmp_seq=4 ttl=64 time=0.502 ms
— 2001:288:a229:1::250 ping statistics —
4 packets transmitted, 4 received, 0% packet loss, time 3004ms
rtt min/avg/max/mdev = 0.470/0.818/1.800/0.567 ms