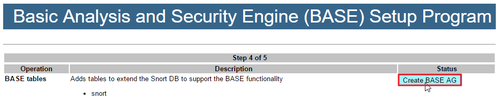
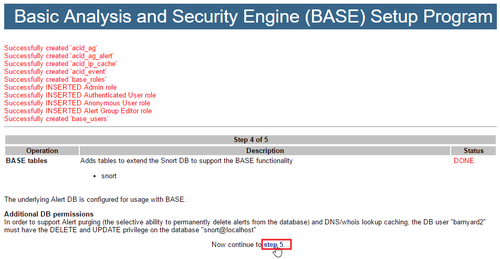
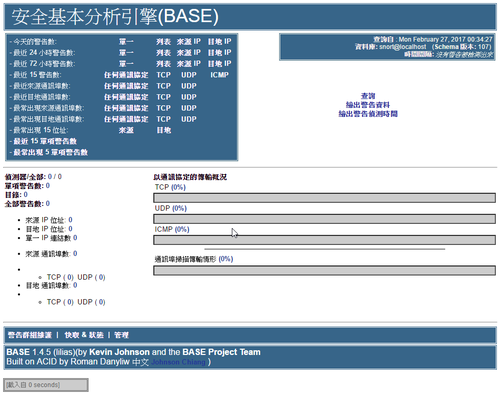
Suricata 和 Snort 一樣,都是入侵偵測系統,二者之間的差異可以參考:
Snort vs Suricata – Aanval Wiki
Suricata 官方網站:https://oisf.net/suricata/
參考網站:
浮雲雅築: [研究] Suricata 3.0 入侵偵測系統安裝 (CentOS 7.2 x64)
如何在 Linux 系統上安裝 Suricata 入侵檢測系統 – 每日頭條
Building an IDS on CentOS using Suricata
CentOS Installation – Suricata – Open Information Security Foundation
IT Security through Open Source : Suricata – wildcard rule loading
1. 利用 epel 套件庫安裝 Suricata
# yum install suricata –enablerepo=epel[@more@]2. 下載 rules 並解壓縮
# wget http://rules.emergingthreats.net/open/suricata/emerging.rules.tar.gz
# tar xvzf suricata/emerging.rules.tar.gz -C /etc/suricata
3. 測試設定檔 /etc/suricata/suricata.yaml
# /sbin/suricata -T -c /etc/suricata/suricata.yaml -i eth0
1/3/2017 — 14:50:53 – <Info> – Running suricata under test mode
1/3/2017 — 14:50:53 – <Notice> – This is Suricata version 3.2.1 RELEASE
1/3/2017 — 14:50:56 – <Notice> – Configuration provided was successfully loaded. Exiting.
如果沒有做第二步驟,會有一些 Warning
# /sbin/suricata -T -c /etc/suricata/suricata.yaml -i eth0
1/3/2017 — 14:16:50 – <Info> – Running suricata under test mode
1/3/2017 — 14:16:50 – <Notice> – This is Suricata version 3.2.1 RELEASE
1/3/2017 — 14:16:50 – <Warning> – [ERRCODE: SC_ERR_NO_RULES(42)] – No rule files match the pattern /etc/suricata/rules/botcc.rules
1/3/2017 — 14:19:04 – <Warning> – [ERRCODE: SC_ERR_NO_RULES(42)] – No rule files match the pattern /etc/suricata/rules/ciarmy.rules
1/3/2017 — 14:19:32 – <Warning> – [ERRCODE: SC_ERR_NO_RULES(42)] – No rule files match the pattern /etc/suricata/rules/compromised.rules
1/3/2017 — 14:20:18 – <Warning> – [ERRCODE: SC_ERR_NO_RULES(42)] – No rule files match the pattern /etc/suricata/rules/drop.rules
4. 因為使用 systemctl 一直無法正常啟動
# mv /usr/lib/systemd/system/suricata.service /root
5. 所以自行建立啟動檔 /etc/init.d/suricatd
# vim /etc/init.d/suricatad
#!/bin/sh
# $Id$
#
# suricatad Start/Stop the suricata IDS daemon.
#
# chkconfig: 2345 40 60
# description: Suricata is a lightweight network intrusion detection tool that
# currently detects more than 1100 host and network
# vulnerabilities, portscans, backdoors, and more.
#
# Source function library.
. /etc/rc.d/init.d/functions
# See how we were called.
case “$1” in
start)
echo -n “Starting Suricata: “
daemon PCAP_FRAMES=max /sbin/suricata -D -c /etc/suricata/suricata.yaml -i eth0
;;
stop)
echo -n “Stopping Suricata: “
killproc suricata
echo
;;
restart)
$0 stop
$0 start
;;
status)
status suricata
;;
*)
echo “Usage: $0 {start|stop|restart|status|}”
exit 1
esac
exit 0
6. 設定檔案權限
# chmod +x /etc/init.d/suricatad
7. 設定開機時啟動
# chkconfig –add suricatad
# /etc/init.d/suricatad start
# /etc/init.d/suricatad status
● suricatad.service – SYSV: Suricata is a lightweight network intrusion detection tool that currently detects more than 1100 host and network vulnerabilities, portscans, backdoors, and more.
Loaded: loaded (/etc/rc.d/init.d/suricatad; bad; vendor preset: disabled)
Active: active (running) since Wed 2017-03-01 15:10:45 CST; 3min 58s ago
Docs: man:systemd-sysv-generator(8)
CGroup: /system.slice/suricatad.service
mq311 /sbin/suricata -D -c /etc/suricata/suricata.yaml -i eth0
Mar 01 15:10:45 ids systemd[1]: Starting SYSV: Suricata is a lightweight network intrusion detection tool that currently detects more than 1100 host and network vulnerabilities, portscans, back…s, and more….
Mar 01 15:10:45 ids suricatad[308]: Starting Suricata: 1/3/2017 — 07:10:45 – <Notice> – This is Suricata version 3.2.1 RELEASE
Mar 01 15:10:45 ids suricatad[308]: [ OK ]
Mar 01 15:10:45 ids systemd[1]: Started SYSV: Suricata is a lightweight network intrusion detection tool that currently detects more than 1100 host and network vulnerabilities, portscans, backdoors, and more..
Hint: Some lines were ellipsized, use -l to show in full.