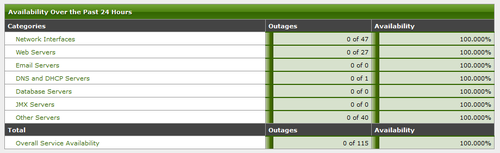
OpenNMS 是一套 OpenSource 的網路管理軟體,可以利用 Ping 及 SNMP 的方式來偵測網路設備或服務的啟動狀態。
OpenNMS 官方網站:http://www.opennms.org/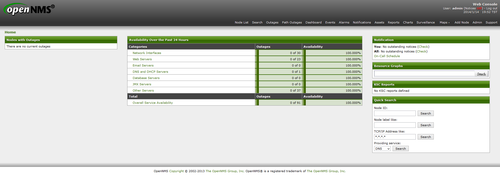 本篇文章參考:浮雲雅築: [研究] OpenNMS 1.12.3 快速安裝程式 (yum)(CentOS 6.5 x64)
本篇文章參考:浮雲雅築: [研究] OpenNMS 1.12.3 快速安裝程式 (yum)(CentOS 6.5 x64)
[@more@]
下載 OpenNMS 套件庫 rpm
# wget http://yum.opennms.org/repofiles/opennms-repo-stable-rhel6.noarch.rpm
進行安裝
# rpm -Uvh opennms-repo-stable-rhel6.noarch.rpm
安裝 PostgreSQL 資料庫
# yum install postgresql postgresql-server
PostgreSQL 初始化資料庫
# service postgresql initdb
正在初始化資料庫: [ 確定 ]
啟動 PostgreSQL Server
# service postgresql start
正在啟動 postgresql 服務: [ 確定 ]
如果沒有先初始化資料庫,而直接啟動,則會出現下面的錯誤訊息
# service postgresql start
/var/lib/pgsql/data is missing. Use “service postgresql initdb” to initialize the cluster first.
[失敗]
設定開機時啟動
# chkconfig –level 3 postgresql on
先備份設定檔,再進行修改
# cp /var/lib/pgsql/data/pg_hba.conf /var/lib/pgsql/data/pg_hba.conf.$(date +%F)
將 70 行後的 ident 取代成 trust
# sed -i ’70,$s/ident/trust/’ /var/lib/pgsql/data/pg_hba.conf
重新啟動 PostgreSQL Server
# service postgresql restart
正在停止 postgresql 服務: [ 確定 ]
正在啟動 postgresql 服務: [ 確定 ]
檢查是否有正常啟動 PostgreSQL Server
# netstat -antulp | grep 5432
tcp 0 0 127.0.0.1:5432 0.0.0.0:* LISTEN 8092/postmaster
tcp 0 0 ::1:5432 :::* LISTEN 8092/postmaster
安裝 Oracle Java JDK
Oracle Java JDK 下載網頁:
http://www.oracle.com/technetwork/java/javase/downloads/jdk7-downloads-1880260.html
# rpm -ivh jdk-7u45-linux-x64.rpm
進行 Oracle Java JDK 設定
# alternatives –install /usr/bin/java java /usr/java/jdk1.7.0_45/bin/java 100
# alternatives –set java /usr/java/jdk1.7.0_45/bin/java
# echo ‘export JAVA_HOME=/usr/java/jdk1.7.0_45’ >> /etc/profile
# echo ‘export PATH=$PATH:$JAVA_HOME/bin’ >> /etc/profile
# echo ‘export CLASSPATH=$JAVA_HOME/jre/lib/ext:$JAVA_HOME/lib/tools.jar’ >> /etc/profile
# source /etc/profile
檢查 Java 版本
# java -version
java version “1.7.0_45”
Java(TM) SE Runtime Environment (build 1.7.0_45-b18)
Java HotSpot(TM) 64-Bit Server VM (build 24.45-b08, mixed mode)
安裝 OpenNMS
# yum -y install opennms opennms-plugins opennms-remote-poller mib2opennms iplike
*** Installation complete. You must still run the installer at
*** $OPENNMS_HOME/bin/install to be sure your database is up
*** to date before you start OpenNMS. See the install guide at
*** http://www.opennms.org/wiki/Installation:RPM and the
*** release notes for details.
設定 OpenNMS 環境變數
# export OPENNMS_HOME=/opt/opennms
# echo ‘export PATH=$PATH:$OPENNMS_HOME/bin’ >> /etc/profile
設定 OpenNMS 使用的 Java
# /opt/opennms/bin/runjava -S /usr/java/latest/bin/java
runjava: checking specified JRE: “/usr/java/latest/bin/java”…
runjava: specified JRE is good.
runjava: value of “/usr/java/latest/bin/java” stored in configuration file
# $OPENNMS_HOME/bin/runjava -s
runjava: Looking for an appropriate JRE…
runjava: Checking for an appropriate JRE in JAVA_HOME…
runjava: found: “/usr/java/jdk1.7.0_45/bin/java” is an appropriate JRE
runjava: value of “/usr/java/jdk1.7.0_45/bin/java” stored in configuration file
建立 OpenNMS 需要的資料庫
# $OPENNMS_HOME/bin/install -dis
最後會出現
Upgrade completed successfully!
啟動 OpenNMS
# service opennms start
Starting OpenNMS: Started OpenNMS, but it has not finished starting up
[失敗]
設定開機時啟動
# chkconfig –level 3 opennms on
雖然最後的訊息出現失敗,但有正常執行
# netstat -antulp | grep 8980
tcp 0 0 :::8980 :::* LISTEN 8956/java
tcp 0 0 :::18980 :::* LISTEN 8956/java
如果不放心,可以檢查 log 檔的訊息
# cat /opt/opennms/logs/daemon/output.log
[DEBUG] System property ‘opennms.library.jicmp’ set to ‘/usr/lib64/libjicmp.so. Attempting to load jicmp library from this location.
[INFO] Successfully loaded jicmp library.
[DEBUG] System property ‘opennms.library.jicmp6’ set to ‘/usr/lib64/libjicmp6.so. Attempting to load jicmp6 library from this location.
[INFO] Successfully loaded jicmp6 library.
顯示 OpenNMS 執行狀態
# /opt/opennms/bin/opennms -v status
OpenNMS.Eventd : running
OpenNMS.Trapd : running
OpenNMS.Queued : running
OpenNMS.Actiond : running
OpenNMS.Notifd : running
OpenNMS.Scriptd : running
OpenNMS.Rtcd : running
OpenNMS.Pollerd : running
OpenNMS.PollerBackEnd : running
OpenNMS.Ticketer : running
OpenNMS.Collectd : running
OpenNMS.Discovery : running
OpenNMS.Vacuumd : running
OpenNMS.EventTranslator: running
OpenNMS.PassiveStatusd : running
OpenNMS.Statsd : running
OpenNMS.Provisiond : running
OpenNMS.Reportd : running
OpenNMS.Alarmd : running
OpenNMS.Ackd : running
OpenNMS.JettyServer : running
opennms is running
開啟瀏覽器,在網址列上輸入 http://Server’IP:8980/opennms
預設帳號和密碼都是 admin,可以在 Web 介面中更改密碼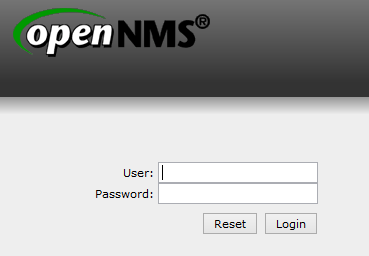
設定 OpenNMS 要偵測的網段,也可以在 Web 介面設定
# vim /opt/opennms/etc/discovery-configuration.xml
<discovery-configuration threads=”1″ packets-per-second=”1″
initial-sleep-time=”30000″ restart-sleep-time=”86400000″
retries=”1″ timeout=”2000″>
<include-range>
<begin>192.168.1.1</begin>
<end>192.168.1.254</end>
</include-range>
</discovery-configuration>
在防火牆中設定
iptables -A INPUT -p tcp -m state –state NEW –dport 389 -j ACCEPT