參考網頁:
使用 Chrony 調校系統時間 | TechNote
XYZ的筆記本: CentOS 7 自動校時(使用chrony)
[Linux] 在 CentOS 7 上使用預設的 chrony 套件來設定 NTP 自動對時 @ 亂打一通的心情日記 :: 痞客邦 PIXNET ::
1. 安裝 chrony
# yum install chrony
2. 啟動 chronyd 服務
# systemctl start chronyd.service
3. 檢查 chronyd 執行狀態
# systemctl status chronyd.service
● chronyd.service – NTP client/server
Loaded: loaded (/usr/lib/systemd/system/chronyd.service; enabled; vendor preset: enabled)
Active: active (running) since Tue 2017-03-07 19:33:17 CST; 1 day 12h ago
Main PID: 621 (chronyd)
CGroup: /system.slice/chronyd.service
mq621 /usr/sbin/chronyd
Mar 07 19:33:17 proxy.tces.ilc.edu.tw systemd[1]: Starting NTP client/server…
Mar 07 19:33:17 proxy.tces.ilc.edu.tw chronyd[621]: chronyd version 2.1.1 starting (+CMDMON +NTP +REFCLOCK +RTC +PRIVDROP +DEBUG +ASYNCDNS +IPV6 +SECHASH)
Mar 07 19:33:17 proxy.tces.ilc.edu.tw chronyd[621]: Frequency 14.920 +/- 0.049 ppm read from /var/lib/chrony/drift
Mar 07 19:33:17 proxy.tces.ilc.edu.tw systemd[1]: Started NTP client/server.
Mar 07 19:33:31 proxy.tces.ilc.edu.tw chronyd[621]: Selected source 103.18.128.60
Mar 07 19:33:31 proxy.tces.ilc.edu.tw chronyd[621]: System clock wrong by -0.711733 seconds, adjustment started[@more@]
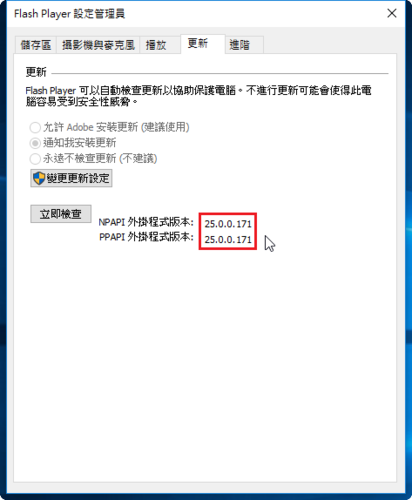
4. 檢查 NTP 來源狀態
# /usr/bin/chronyc sourcestats
210 Number of sources = 4
Name/IP Address NP NR Span Frequency Freq Skew Offset Std Dev
==============================================================================
123-204-45-116.static.see 7 5 103m +0.033 0.269 -103us 221us
211-79-171-1.ip.rpb.gov.t 6 4 86m -0.102 1.012 -186us 521us
2001:288:b012::2 4 3 51m -0.089 2.182 -274us 112us
103-18-128-60.ip.mwsrv.co 5 5 69m -0.096 0.661 -26us 176us
5. 查看 NTP 詳細同步狀態
# /usr/bin/chronyc sources -v
210 Number of sources = 4
.– Source mode ‘^’ = server, ‘=’ = peer, ‘#’ = local clock.
/ .- Source state ‘*’ = current synced, ‘+’ = combined , ‘-‘ = not combined,
| / ‘?’ = unreachable, ‘x’ = time may be in error, ‘~’ = time too variable.
|| .- xxxx [ yyyy ] +/- zzzz
|| Reachability register (octal) -. | xxxx = adjusted offset,
|| Log2(Polling interval) –. | | yyyy = measured offset,
|| | | zzzz = estimated error.
|| | |
MS Name/IP address Stratum Poll Reach LastRx Last sample
===============================================================================
^+ 123-204-45-116.static.see 3 10 377 21 +1642us[+1642us] +/- 67ms
^- 211-79-171-1.ip.rpb.gov.t 3 10 377 961 -13us[ -13us] +/- 83ms
^- 2001:288:b012::2 3 10 377 472 -808us[ -808us] +/- 62ms
^* 103-18-128-60.ip.mwsrv.co 2 10 377 973 +35us[ -53us] +/- 34ms
6. 查看對時狀況
# /usr/bin/chronyc tracking
Reference ID : 103.18.128.60 (103-18-128-60.ip.mwsrv.com)
Stratum : 3
Ref time (UTC) : Thu Mar 9 00:17:01 2017
System time : 0.000047602 seconds slow of NTP time
Last offset : +0.000010441 seconds
RMS offset : 0.000198219 seconds
Frequency : 14.958 ppm fast
Residual freq : -0.003 ppm
Skew : 0.227 ppm
Root delay : 0.009934 seconds
Root dispersion : 0.028548 seconds
Update interval : 1027.3 seconds
Leap status : Normal
7. 使用 chrony 立刻對時
# /usr/bin/chronyc -a makestep
200 OK
200 OK