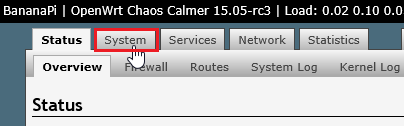
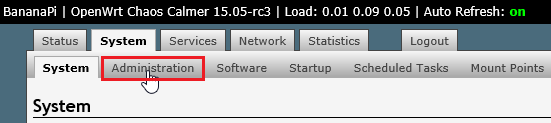
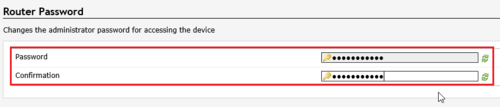
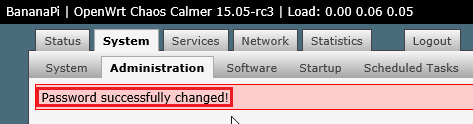
關於 OpenConnect 可以參考:
用樹莓派架設SSL VPN 最低成本打造窮人翻牆梯 – 技術專欄 – 網管人NetAdmin
本篇文章參考:
CentOS 7 安装 ocserv (OpenConnect Server) 并实现证书登录 – 奇遇·奇玉
在 CentOS 7 上搭建 Cisco AnyConnect VPN · ifreedomlife
老天尊的死期: Linode CentOS 7主機搭建Cisco AnyConnect VPN
1. 新增 epel 套件庫
# yum install epel-release
2. 更新套件庫
# yum update[@more@]3. 安裝 ocserv 套件
# yum install ocserv
4. 建立目錄及切換目錄
# mkdir certificates
# cd certificates
5. 建立 CA 金鑰
# certtool –generate-privkey –outfile ca-key.pem
Generating a 2048 bit RSA private key…
建立 ca.tmpl
# cat ca.tmpl
cn = “VPN CA”
organization = “Home”
serial = 1
expiration_days = 3650
ca
signing_key
cert_signing_key
crl_signing_key
# certtool –generate-self-signed –load-privkey ca-key.pem –template ca.tmpl –outfile ca-cert.pem
複製 ca-cert.pem 到 /etc/ocserv 目錄
# cp ca-cert.pem /etc/ocserv
6. 建立本機 Server 證書
# certtool –generate-privkey –outfile server-key.pem
Generating a 2048 bit RSA private key…
建立 server.tmpl
# cat server.tmpl
cn = “nas.test.com”
organization = “Home”
serial = 2
expiration_days = 3650
encryption_key
signing_key
tls_www_server
# certtool –generate-certificate –load-privkey server-key.pem –load-ca-certificate ca-cert.pem –load-ca-privkey ca-key.pem –template server.tmpl –outfile server-cert.pem
將 server-cert.pem 和 server-key.pem 複製到 /etc/ocserv
# cp server-cert.pem server-key.pem /etc/ocserv
7. 產生使用者端證書(連線時可以輸入帳號及密碼)
# cat gen-client-cert.sh
#!/bin/bash
USER=$1
CA_DIR=$2
SERIAL=`date +%s`
certtool –generate-privkey –outfile $USER-key.pem
cat << _EOF_ >user.tmpl
cn = “$USER”
unit = “users”
serial = “$SERIAL”
expiration_days = 9999
signing_key
tls_www_client
_EOF_
certtool –generate-certificate –load-privkey $USER-key.pem –load-ca-certificate $CA_DIR/ca-cert.pem –load-ca-privkey $CA_DIR/ca-key.pem –template user.tmpl –outfile $USER-cert.pem
openssl pkcs12 -export -inkey $USER-key.pem -in $USER-cert.pem -name “$USER VPN Client Cert” -certfile $CA_DIR/ca-cert.pem -out $USER.p12
更改檔案權限
# chmod 700 gen-client-cert.sh
建立目錄來存放使用者證書
# mkdir home
# 切換目錄
# cd home
# home 是使用者的名稱,.. 是指 ca 證書所在的目錄
# ../gen-client-cert.sh home ..
可以直接按 Enter 鍵跳過,就不用設定密碼
Signing certificate…
Enter Export Password:
Verifying – Enter Export Password:
產生之後可以將 home.p12 複製給使用者用戶端導入即可
8. 修改 /etc/ocserv/ocserv.conf 設定檔
# cp /etc/ocserv/ocserv.conf /etc/ocserv/ocserv.conf.$(date +%F)
取消 pam 認證
# sed -i ‘s/auth = “pam”/#auth = “pam”/’ /etc/ocserv/ocserv.conf
採用 certificate 認證
# sed -i ‘s/#auth = “certificate”/auth = “certificate”/’ /etc/ocserv/ocserv.conf
設定同一個用戶最多的登入數
# sed -i ‘s/max-same-clients = 2/max-same-clients = 10/’ /etc/ocserv/ocserv.conf
設定憑證檔的位置
# sed -i ‘s|#server-cert = /etc/pki/ocserv/public/server.crt|server-cert = /etc/ocserv/server-cert.pem|’ /etc/ocserv/ocserv.conf
# sed -i ‘s|#server-key = /etc/pki/ocserv/private/server.key|server-key = /etc/ocserv/server-key.pem|’ /etc/ocserv/ocserv.conf
# sed -i ‘s|#ca-cert = /etc/pki/ocserv/cacerts/ca.crt|ca-cert = /etc/ocserv/ca-cert.pem|’ /etc/ocserv/ocserv.conf
從證書中提取用戶名的方式,這裡提取的是證書中的 CN 欄位作為用戶名
# sed -i ‘s/cert-user-oid = 0.9.2342.19200300.100.1.1/cert-user-oid = 2.5.4.3/’ /etc/ocserv/ocserv.conf
分配給 VPN 用戶端的 IP 網段
# sed -i ‘s/#ipv4-network = 192.168.1.0/ipv4-network = 10.12.0.0/’ /etc/ocserv/ocserv.conf
# sed -i ‘s/#ipv4-netmask = 255.255.255.0/ipv4-netmask = 255.255.255.0/’ /etc/ocserv/ocserv.conf
設定 DNS
# sed -i ‘s/#dns = 192.168.1.2/dns = 8.8.8.8/’ /etc/ocserv/ocserv.conf
# 解決 GnuTLS error (at worker-vpn.c 問題
# sed -i ‘s/isolate-workers = true/isolate-workers = false/’ /etc/ocserv/ocserv.conf
9. 設定網路 Forward
# echo “net.ipv4.ip_forward = 1” >> /etc/sysctl.conf
# sysctl -p /etc/sysctl.conf
10. 設定防火牆規則
# iptables -t nat -A POSTROUTING -s 10.12.0.0/24 -o eth0 -j MASQUERADE
# iptables -A FORWARD -i vpns+ -j ACCEPT
# iptables -A FORWARD -o vpns+ -j ACCEPT
11. 儲存防火牆規則
# iptables-save > /etc/sysconfig/iptables
12. 設定開機時啟動
# systemctl enable ocserv
Created symlink from /etc/systemd/system/multi-user.target.wants/ocserv.service to /usr/lib/systemd/system/ocserv.service.
12. 啟動 OpenConnect Server
# systemctl start ocserv
# systemctl status ocserv