Pure-FTPd FTP Server 也可以搭配 MySQL 的虛擬帳號來登入
首先安裝 MySQL Server
# yum install mysql mysql-server
啟動 MySQL Server
# service mysqld start
設定 MySQL Server
# /usr/bin/mysql_secure_installation[@more@]設定 Pure-FTPd FTP Server
# vim /etc/pure-ftpd/pure-ftpd.conf
# MySQL configuration file (see README.MySQL)
MySQLConfigFile /etc/pure-ftpd/pureftpd-mysql.conf
設定 Pure-FTPd FTP Server 的 MySQL 設定檔
# vim /etc/pure-ftpd/pureftpd-mysql.conf
# Optional : define the location of mysql.sock if the server runs on this host.
# MySQL Socket 檔路徑
MYSQLSocket /var/lib/mysql/mysql.sock
# Mandatory : user to bind the server as.
# MySQL 管理者
MYSQLUser root
# Mandatory : user password. You must have a password.
# MySQL 管理者密碼
MYSQLPassword rootpw
# Mandatory : database to open.
# Pure-FTPd 要用的資料庫檔名
MYSQLDatabase pureftpd
# Mandatory : how passwords are stored
# Valid values are : “cleartext”, “crypt”, “md5” and “password”
# (“password” = MySQL password() function)
# You can also use “any” to try “crypt”, “md5” *and* “password”
# 密碼編碼的方式,可以使用 cleartext 明碼 / md5 使用 MD5 編碼加密 / crypt 用 DES 編碼加密 / password MySQL 的編碼加密
MYSQLCrypt cleartext
# Query to execute in order to fetch the password
# 虛擬帳號符合 User 欄位時,選取登入者的密碼欄位
MYSQLGetPW SELECT Password FROM users WHERE User=’L’
# Query to execute in order to fetch the system user name or uid
# 當虛擬帳號符合 User 欄位時,選取登入者的使用者 ID
MYSQLGetUID SELECT Uid FROM users WHERE User=’L’
# Optional : default UID – if set this overrides MYSQLGetUID
#MYSQLDefaultUID 500
# Query to execute in order to fetch the system user group or gid
# 當虛擬帳號符合 User 欄位時,選取登入者的群組 ID
MYSQLGetGID SELECT Gid FROM users WHERE User=’L’
# Optional : default GID – if set this overrides MYSQLGetGID
# 內定的群組 GID
#MYSQLDefaultGID 500
# Query to execute in order to fetch the home directory
# 當虛擬帳號符合 User 欄位時,選取登入者的家目錄
MYSQLGetDir SELECT Dir FROM users WHERE User=’L’
重新啟動 Pure-FTPd FTP Server
# /etc/init.d/pure-ftpd restart
建立資料庫
# vim /root/pureftpd.sql
CREATE TABLE users (
User VARCHAR(16) BINARY NOT NULL,
Password VARCHAR(64) BINARY NOT NULL,
Uid INT(11) NOT NULL default ‘-1’,
Gid INT(11) NOT NULL default ‘-1’,
Dir VARCHAR(128) BINARY NOT NULL,
PRIMARY KEY (User)
) ENGINE=MyISAM DEFAULT CHARSET=utf8 COLLATE=utf8_unicode_ci;
insert into users values (‘u0910001′,’abCxyZ’,’500′,’500′,’/home/virtualuser/u0910001′);
insert into users values (‘u0910002′,’QazXsw’,’500′,’500′,’/home/virtualuser/u0910002′);
# /usr/bin/mysqladmin -u root -p create pureftpd
# /usr/bin/mysql -u root -p pureftpd < /root/pureftpd.sql
測試
# mkdir -p /home/virtualuser/{u0910001,u0910002}
# chown -R virtualuser:virtualgrp /home/virtualuser/{u0910001,u0910002}
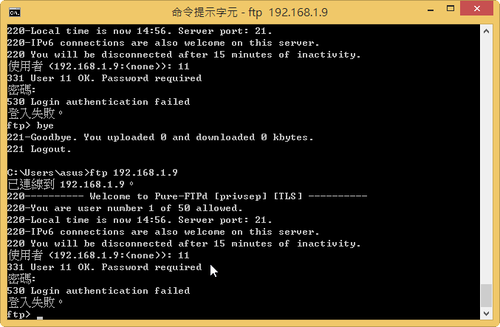
# lftp -u u0910001 192.168.154.167
密碼:
lftp u0910001@192.168.154.167:~> ls -l
drwxr-xr-x 2 500 virtualgrp 4096 Jan 2 10:17 .
drwxr-xr-x 2 500 virtualgrp 4096 Jan 2 10:17 ..
lftp u0910001@192.168.154.167:/>
如果系統有使用 SELinux,要記得把家目錄的功能打開
# setsebool -P ftp_home_dir 1
# setsebool -P allow_ftpd_full_access=1
更複雜的設定
CREATE DATABASE pure-ftpd;
CREATE TABLE `users` (
`id` int(32) unsigned NOT NULL auto_increment,
`User` varchar(16) NOT NULL default ”,
`Password` varchar(64) NOT NULL default ”,
`Uid` varchar(11) NOT NULL default ‘-1’,
`Gid` varchar(11) NOT NULL default ‘-1’,
`Dir` varchar(128) NOT NULL default ”,
`QuotaSize` smallint(5) NOT NULL default ‘0’,
`QuotaFiles` int(11) NOT NULL default ‘0’,
`ULBandwidth` smallint(5) NOT NULL default ‘0’,
`DLBandwidth` smallint(5) NOT NULL default ‘0’,
`ULRatio` smallint(6) NOT NULL default ‘0’,
`DLRatio` smallint(6) NOT NULL default ‘0’,
`comment` tinytext NOT NULL,
`ipaccess` varchar(15) NOT NULL default ‘*’,
`status` enum(‘0′,’1’) NOT NULL default ‘0’,
`create_date` datetime NOT NULL default ‘0000-00-00 00:00:00’,
`modify_date` datetime NOT NULL default ‘0000-00-00 00:00:00’,
PRIMARY KEY (`id`,`User`),
UNIQUE KEY `User` (`User`)
) TYPE=MyISAM AUTO_INCREMENT=5 ;